
Unlock creative excellence with an ai creative agency
AI creative agencies combine cutting-edge technology with artistic insight to deliver tailored marketing, design, and branding solutions. By harnessing big data and predictive analytics, they[…]

Unveiling the transformative power of ai-enhanced custom storylines in interactive story games
Unveiling the Transformative Power of AI-Enhanced Custom Storylines in Interactive Story Games The gaming industry has undergone a significant transformation with the integration of artificial[…]
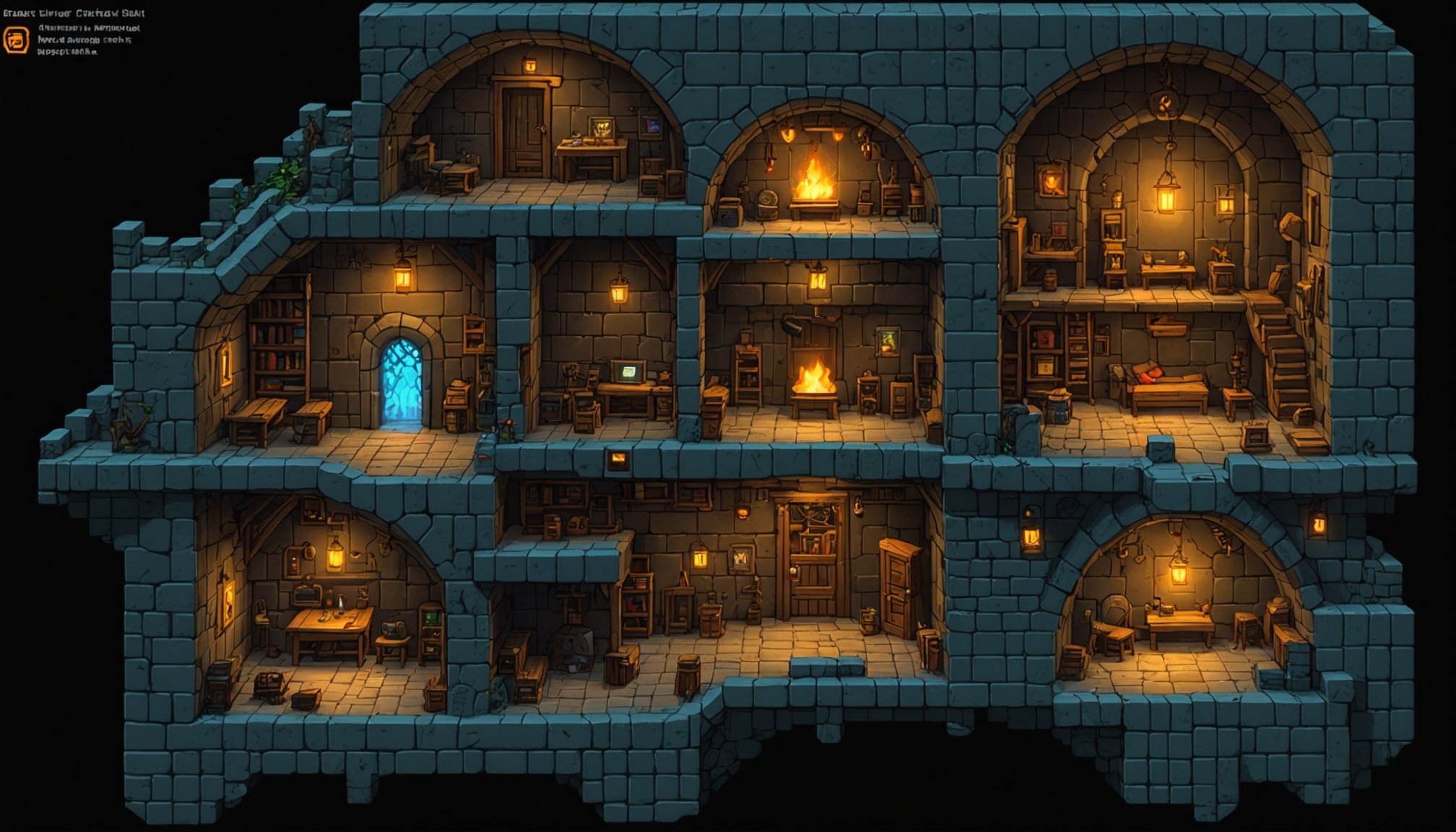
Discovering algorithmic enchantment: leveraging ai for one-of-a-kind level design in roguelike adventures
Understanding Algorithmic Design Principles in Game Development In the realm of game development principles, algorithmic design is foundational. It encompasses the methodologies used to guide[…]

Transforming UK Fashion Retail: Unlocking the Power of Augmented Reality for Unforgettable Online Shopping Experiences
Introduction to Augmented Reality in UK Fashion Retail Augmented Reality (AR) has become a game-changer in UK fashion retail, significantly enhancing the online shopping experience.[…]

Mastering High-Availability: The Definitive Blueprint for Creating a Robust Redis Cluster with Redis Sentinel
Understanding Redis Sentinel and High Availability Redis Sentinel plays a pivotal role in maintaining high availability of your Redis services. It provides automatic failover to[…]

Effective Strategies for Building a Robust Real-Time Fraud Detection System with Machine Learning
Overview of Real-Time Fraud Detection Systems Real-time fraud detection systems are essential tools for financial safety, designed to identify fraudulent activities instantly and prevent losses.[…]

Transforming Patient Care in the UK: The Impact of Telemedicine on Health Outcomes
Overview of Telemedicine in the UK The evolution of telemedicine post-pandemic has significantly transformed the UK healthcare system. Initially sparked by necessity, telemedicine adoption has[…]

Mastering Dual-Boot: Your Comprehensive Guide to Seamlessly Install Windows 10 and Linux Mint on Your HP Pavilion Laptop
Prerequisites for Dual-Booting Before diving into a dual-boot setup with Windows 10 and Linux Mint, it’s crucial to verify your system requirements. Both operating systems[…]

Maximizing Elasticsearch Performance: Proven Strategies to Enhance Query Speed on Massive Datasets
Understanding Elasticsearch Performance Elasticsearch Architecture and Its Role Elasticsearch performance is directly influenced by its architecture, a distributed system designed for processing vast amounts of[…]

Exploring the impact of gpu size on cooling performance: what you need to know
Understanding GPU Size and Architecture In the world of graphics processing units (GPUs), GPU architecture and GPU size play pivotal roles in determining performance and[…]










